Feature Blogs
Security teams today face an overwhelming number of alerts, repetitive tasks, and complex incident response processes. To handle this efficiently, organizations rely on SOAR (Security Orchestration...
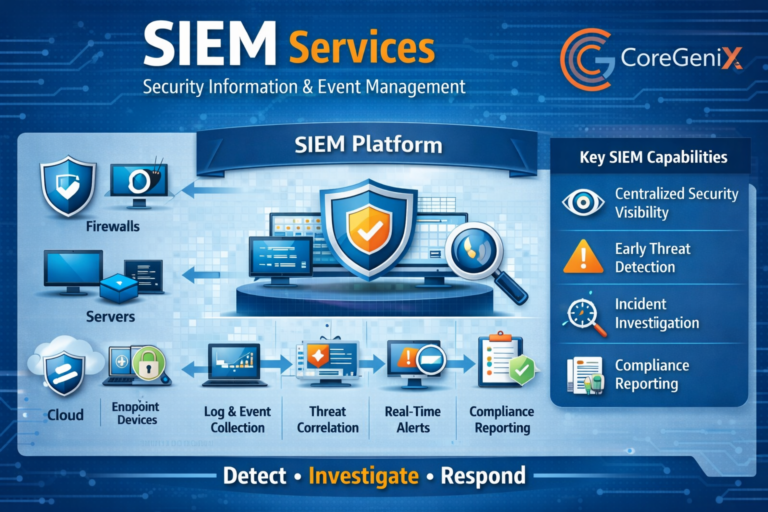
Modern organizations generate massive volumes of security data every second. Logs, alerts, and events from multiple systems make it difficult to identify real threats. This is where SIEM (Security...
With the rise of remote work, BYOD (Bring Your Own Device), and mobile-first businesses, managing and securing mobile devices has become a critical challenge. This is where Mobile Device Management...
As cyber threats become more sophisticated, traditional security tools are no longer sufficient. Organizations now need advanced, unified security solutions to detect and respond to attacks across...
In today’s digital-first world, cyberattacks no longer target only servers or networks—they target endpoints. Laptops, desktops, mobile devices, and even IoT systems are now prime entry points for...
In today’s complex IT environments, cyber threats no longer come from a single source. Attacks can originate from endpoints, networks, cloud platforms, applications, or even user behavior. Managing...
In today’s digital world, cyberattacks are becoming more advanced and frequent. Traditional antivirus solutions are no longer enough to protect businesses from ransomware, zero-day attacks, and...
In today’s digital environment, cyberattacks most commonly enter organizations through endpoints—such as employee laptops, desktops, and servers. With the rise of remote work, cloud access, and...
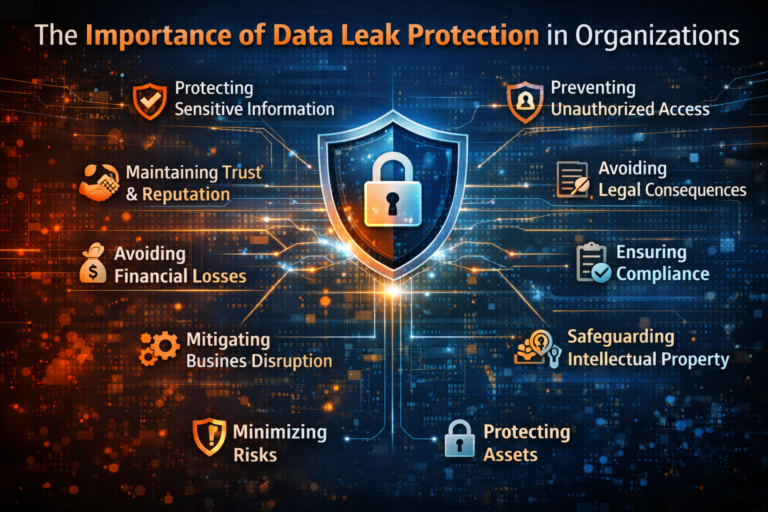
In today’s digital age, the protection of confidential information and data is of utmost importance for organizations. With the increasing number of cyber threats and data breaches, businesses...